With the use of threat modeling software, teams can detect, and prioritize threats for mitigation early in the DevOps practice, during the initial design and development stages, saving organizations valuable time and effort. AIIT works with your team to design threat models following the visual, agile, industry standard methodology to provide actionable outcomes for DevOps to easily conduct risk assessments and address threats for more secure environments.
Security Architecture Review & Threat Modeling
- Home /
- Security Architecture Review & Threat Modeling
Security Architecture Review & Threat Modeling
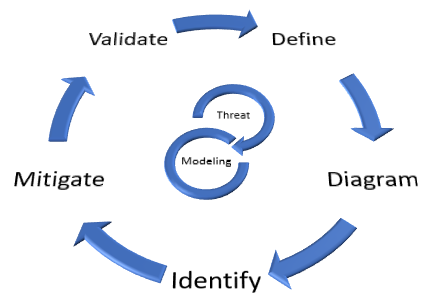
Key activities include:
- Define Business Objectives
- Identify application design
- Review design documents
- Decompose and Model the System
- Define and Evaluate your Assets
- Create an information flow diagram
- Identify Threat Agents
- Create Threat traceability matrix
- Rank Risks
- Determine countermeasures and mitigation

